HTTP | OAuth2
OAuth2 allows third-party applications to receive a limited access to an HTTP service which is either on behalf of a resource owner or by allowing a third-party application obtain access on its own behalf. Thanks to OAuth2, service providers and consumer applications can interact with each other in a secure way.
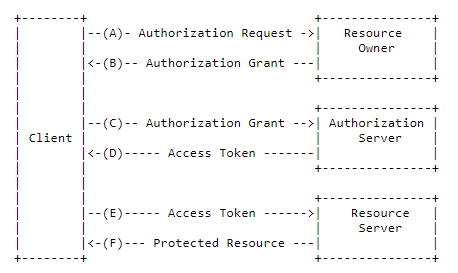
In OAuth2, there are 4 roles:
- Resource Owner: the user.
-
Resource Server: the server that hosts the protected resources and provides access to it based on the access token.
- Client: the external application that seeks permission.
- Authorization Server: issues the access token after having authenticated the user.
Components
- TsgcHTTP_OAuth2_Client: is a client with support for OAuth2, so it can connect to OAuth2 servers to request an authentication like Google, Facebook...
- TsgcHTTP_OAuth2_Server: is the server implementation of OAuth2 protocol, allows you to protect the resources of the Server.
- TsgcHTTP_OAuth2_Server_Provider: allows implementing external OAuth2 Providers (like Azure AD, Google, Facebook...) in your Server, so the user can login using the Azure, Google, Facebook... user credentials.
Server and Client OAuth2 components supports PKCE (Proof Key for Code Exchange), which is an extension to the Authorization Code flow to prevent CSRF and authorization code injection attacks (RFC 7636).